Who Sent This Email?
Ever had someone tell you that you have sent them a suspicious email or that your computer is infected with a virus because it is sending out junk emails?
It is one of the more common problems that I get asked to investigate so if it has happened to you then you are not alone. It has even happened to me. In this blog I will explain what is happening and why you will not be able to do anything about it.
It is one of the more common problems that I get asked to investigate so if it has happened to you then you are not alone. It has even happened to me. In this blog I will explain what is happening and why you will not be able to do anything about it.
Let’s start by looking at a typical example of an email that appears to have been sent by someone called John V.
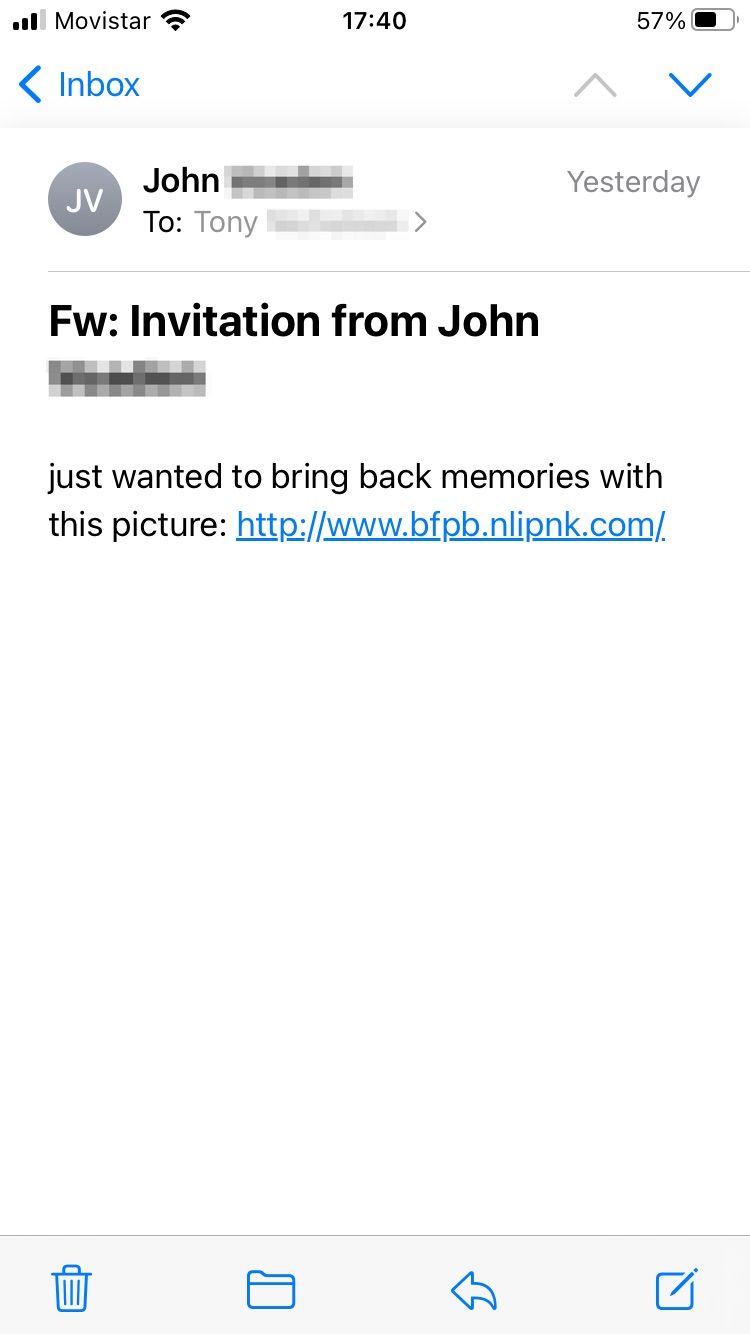
John V sent me this screenshot that the recipient had sent to him, and you can see that the recipient of this email has opened it on a mobile device; in this case a smartphone.
If you regularly open emails on mobile devices (smartphones or tablets) then you need to be aware that these devices will normally show a personal name of the sender and not the senders email address. This makes it really difficult to quickly spot a fake sender email and because of this the scammers will be hoping that recipients will be using mobile devices.
To understand why the scammers prefer recipients to view emails on mobile devices you need to know how easy it is to fake a senders name so let me show you.
Name, Address or Both
Let’s imagine that there is someone called Robert Smith who has r.smith77@gmail.com as his email address. To his many friends he is known as Bob Smith so in his email system he has added Bob Smith as his display name. In Gmail it is called a Display Name but in other email systems it will often be called something else like Nickname, Personal Name or just Name. When Robert sends out an email it will include both his email address and also his display name; Bob Smith.
It is up to each email client to decide what is displayed when the recipient looks at the email. So a recipient could see the sender shown as:
r.smith77@gmail.com
or
Bob Smith (r.smith77@gmail.com)
or
Bob Smith
Clearly if the recipients system displays the first or second options then the recipient can be a lot more certain that the email has been sent by Bob but if it only shows his name and not his email address then the recipient has no way of knowing if it has come from Bob or someone else. It may say it is from Bob Smith but that does not prove that Bob Smith sent the email.
Why is this?
Because anyone sending out an email can put anything they like in the name field but they cannot easily fake the senders email address. Take a look at the email account settings in Apple Mail on my Apple computer:
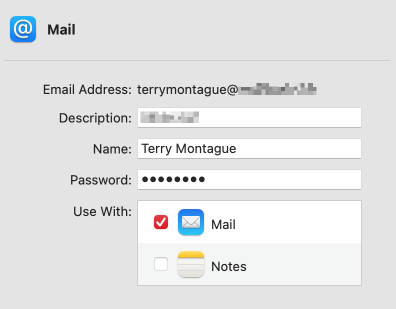
My name is set as Terry Montague so any emails I send out will include this name as well as my email address for the account. A recipient could see the following:
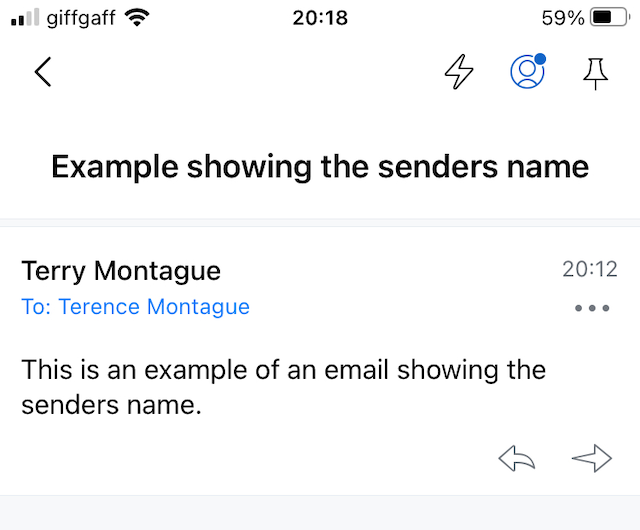
The screenshot above shows an email sent from my personal email account to my business email address and displayed on my mobile phone. You can see the senders name is displayed as Terry Montague because that is the name I set in my Apple Mail settings.
If I view exactly the same email on my Apple computer I see this:
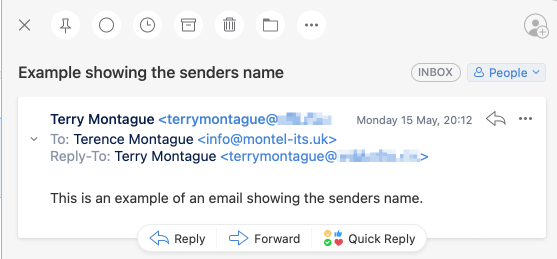
On my computer the email software I am using can display the senders name and also the senders email address. That makes it much easier for me to see that the senders name and email address are what I would expect them to be.
Now take a look at what happens when I change my name to something else and send an email. Here is the name I am going to use:
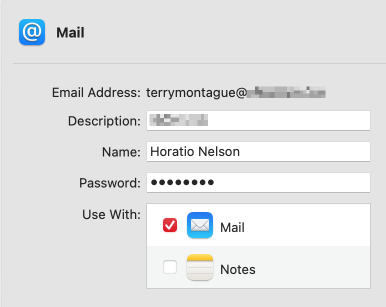
And here is the email I received as displayed on my mobile phone:
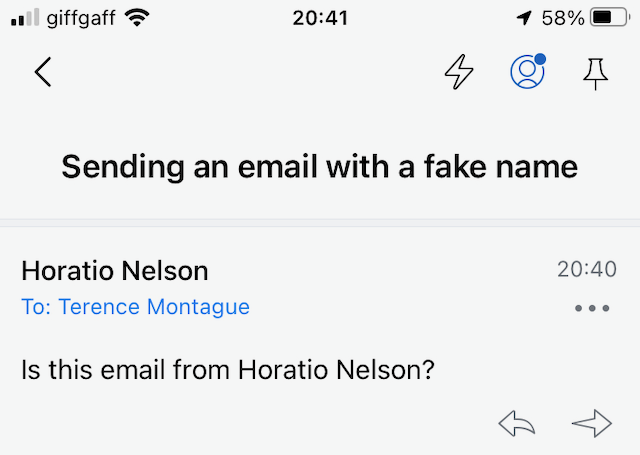
You should be able to see clearly that on my mobile phone it appears that Horatio Nelson has sent me an email. Here is the same email as displayed on my computer:
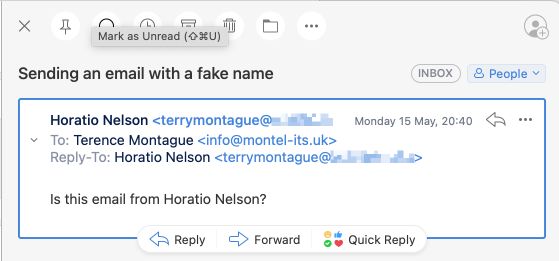
On the computer it is easy to see that the email has not been sent by Horatio Nelson because the senders email address is completely different and clearly not what I would expect it to be. This is why it is so important to be able to see the senders email address and not just the name the sender has chosen to use.
I hope you can see that a scammer can very easily send out emails with any personal name as it has no relationship to the sending address at all. You must never rely on the senders name as proof that the email actually came from them. Ideally you should look at the sending email address as this is much harder to fake. Just remember that if the senders email system has been compromised then even this is not a guarantee that the email is genuine or safe.
If you want to avoid scams and malware then you are going to have to be alert to the tell-tale signs and look for them in every single email you receive.
Does it contain grammatical errors?
Is it unsolicited?
Does it ask you to click on any links embedded in the email?
Does it contain spelling mistakes?
Does it contain any attachments that you are asked to open?
Does it address you by name?
Fake emails seldom include specific details like your name or address as the same email will be sent out to hundreds or thousands of recipients.
All of the things listed above are red flags and the more of them that any email contains the more likely it is that the email is a scam.
However, in Spear Phishing attacks the criminals will be targeting an individual, a specific business or organisation and in these cases they will contain specific details as these are included to convince you that the email is genuine.
How do the criminals get our names?
Unfortunately, there are lots of ways that the scammers can obtain peoples names and these include data stolen from online services and data stolen from peoples own computers. In many examples that I have looked at it is pretty obvious that the scammers have obtained details from a persons email account. This is because the emails coming from the scammer are being sent to individuals known to the person whose name is being used as the sender.
The example email that appears to be from John V has been sent to someone that John V knows so we can be certain that the scammer has obtained this information either from John V’s own email account or from somebody who has both John V’s email details and those of the recipient.
It does not mean that John V’s own computer has been compromised with malware or that the scammer has obtained this information by accessing his computer. It is possible that someone else who happens to have the email details for both John V and the email recipient has had their computer infected with malware that has stolen a copy of their address book. Or their own online email service has been compromised and the details stolen by the scammer.
One example of email details being stolen occurred when Yahoo was hacked all the way back in 2013 although Yahoo didn’t reveal the full extent of the attack until 2017 when they admitted that all three billion customer records had been compromised making it the biggest hack in history. Unfortunately, BT Internet used Yahoo email services for its own customers email service so anyone using BT Internet from 2013 to 2016 will have had their email account details stolen.
I saw a lot of fake sender emails during this time and the majority of them used email accounts that belonged to BT Internet customers. It was painfully obvious to me and many others working in IT support that the email accounts must have been compromised at the service provider but BT maintained that any stolen data had to have come from the customers own devices or online accounts. They only changed their advice when Yahoo publicly admitted that the data had been stolen from them.
If you receive a scam email that appears to have been sent by someone you know then please don’t assume that their device has been hacked or that it has been infected with malware. The scammer has obtained someones name and a list of recipients known to that person and it is the scammer that is sending you the email. There is absolutely nothing that you or the person whose name is being used can do to stop this from happening. You just need to be alert to these scams and delete the emails when they arrive.
After a while the scammers stop sending the emails because they have moved on to using someone else’s stolen details.
See if your email address has been stolen
You can use a free online service to see if your own email address has been stolen in a data hack. Just go to:
https://haveibeenpwned.com
Enter the email address or addresses that you use. The service will check to see if the address is listed in any of the data hacks it knows about. You can also sign up to be notified if an email address you use is found in the future. Another useful service is to be able to check passwords to see if they show up in the database of stolen information.
There isn’t much you can do if your details are listed but at least you will be aware of it and more likely to be on the lookout for suspicious emails sent to you. It should also be less of a surprise if your details get used in one of these fake sender emails.
I know that I say this often but please do NOT use any password for more than one service as that is just asking for trouble. If your details are stolen then criminals will try to use them to access many online services and if you have used the same password then they will be able to access those services.

John V sent me this screenshot that the recipient had sent to him, and you can see that the recipient of this email has opened it on a mobile device; in this case a smartphone.
If you regularly open emails on mobile devices (smartphones or tablets) then you need to be aware that these devices will normally show a personal name of the sender and not the senders email address. This makes it really difficult to quickly spot a fake sender email and because of this the scammers will be hoping that recipients will be using mobile devices.
To understand why the scammers prefer recipients to view emails on mobile devices you need to know how easy it is to fake a senders name so let me show you.
Name, Address or Both
Let’s imagine that there is someone called Robert Smith who has r.smith77@gmail.com as his email address. To his many friends he is known as Bob Smith so in his email system he has added Bob Smith as his display name. In Gmail it is called a Display Name but in other email systems it will often be called something else like Nickname, Personal Name or just Name. When Robert sends out an email it will include both his email address and also his display name; Bob Smith.
It is up to each email client to decide what is displayed when the recipient looks at the email. So a recipient could see the sender shown as:
r.smith77@gmail.com
or
Bob Smith (r.smith77@gmail.com)
or
Bob Smith
Clearly if the recipients system displays the first or second options then the recipient can be a lot more certain that the email has been sent by Bob but if it only shows his name and not his email address then the recipient has no way of knowing if it has come from Bob or someone else. It may say it is from Bob Smith but that does not prove that Bob Smith sent the email.
Why is this?
Because anyone sending out an email can put anything they like in the name field but they cannot easily fake the senders email address. Take a look at the email account settings in Apple Mail on my Apple computer:

My name is set as Terry Montague so any emails I send out will include this name as well as my email address for the account. A recipient could see the following:

The screenshot above shows an email sent from my personal email account to my business email address and displayed on my mobile phone. You can see the senders name is displayed as Terry Montague because that is the name I set in my Apple Mail settings.
If I view exactly the same email on my Apple computer I see this:

On my computer the email software I am using can display the senders name and also the senders email address. That makes it much easier for me to see that the senders name and email address are what I would expect them to be.
Now take a look at what happens when I change my name to something else and send an email. Here is the name I am going to use:

And here is the email I received as displayed on my mobile phone:

You should be able to see clearly that on my mobile phone it appears that Horatio Nelson has sent me an email. Here is the same email as displayed on my computer:

On the computer it is easy to see that the email has not been sent by Horatio Nelson because the senders email address is completely different and clearly not what I would expect it to be. This is why it is so important to be able to see the senders email address and not just the name the sender has chosen to use.
I hope you can see that a scammer can very easily send out emails with any personal name as it has no relationship to the sending address at all. You must never rely on the senders name as proof that the email actually came from them. Ideally you should look at the sending email address as this is much harder to fake. Just remember that if the senders email system has been compromised then even this is not a guarantee that the email is genuine or safe.
If you want to avoid scams and malware then you are going to have to be alert to the tell-tale signs and look for them in every single email you receive.
Does it contain grammatical errors?
Is it unsolicited?
Does it ask you to click on any links embedded in the email?
Does it contain spelling mistakes?
Does it contain any attachments that you are asked to open?
Does it address you by name?
Fake emails seldom include specific details like your name or address as the same email will be sent out to hundreds or thousands of recipients.
All of the things listed above are red flags and the more of them that any email contains the more likely it is that the email is a scam.
However, in Spear Phishing attacks the criminals will be targeting an individual, a specific business or organisation and in these cases they will contain specific details as these are included to convince you that the email is genuine.
How do the criminals get our names?
Unfortunately, there are lots of ways that the scammers can obtain peoples names and these include data stolen from online services and data stolen from peoples own computers. In many examples that I have looked at it is pretty obvious that the scammers have obtained details from a persons email account. This is because the emails coming from the scammer are being sent to individuals known to the person whose name is being used as the sender.
The example email that appears to be from John V has been sent to someone that John V knows so we can be certain that the scammer has obtained this information either from John V’s own email account or from somebody who has both John V’s email details and those of the recipient.
It does not mean that John V’s own computer has been compromised with malware or that the scammer has obtained this information by accessing his computer. It is possible that someone else who happens to have the email details for both John V and the email recipient has had their computer infected with malware that has stolen a copy of their address book. Or their own online email service has been compromised and the details stolen by the scammer.
One example of email details being stolen occurred when Yahoo was hacked all the way back in 2013 although Yahoo didn’t reveal the full extent of the attack until 2017 when they admitted that all three billion customer records had been compromised making it the biggest hack in history. Unfortunately, BT Internet used Yahoo email services for its own customers email service so anyone using BT Internet from 2013 to 2016 will have had their email account details stolen.
I saw a lot of fake sender emails during this time and the majority of them used email accounts that belonged to BT Internet customers. It was painfully obvious to me and many others working in IT support that the email accounts must have been compromised at the service provider but BT maintained that any stolen data had to have come from the customers own devices or online accounts. They only changed their advice when Yahoo publicly admitted that the data had been stolen from them.
If you receive a scam email that appears to have been sent by someone you know then please don’t assume that their device has been hacked or that it has been infected with malware. The scammer has obtained someones name and a list of recipients known to that person and it is the scammer that is sending you the email. There is absolutely nothing that you or the person whose name is being used can do to stop this from happening. You just need to be alert to these scams and delete the emails when they arrive.
After a while the scammers stop sending the emails because they have moved on to using someone else’s stolen details.
See if your email address has been stolen
You can use a free online service to see if your own email address has been stolen in a data hack. Just go to:
https://haveibeenpwned.com
Enter the email address or addresses that you use. The service will check to see if the address is listed in any of the data hacks it knows about. You can also sign up to be notified if an email address you use is found in the future. Another useful service is to be able to check passwords to see if they show up in the database of stolen information.
There isn’t much you can do if your details are listed but at least you will be aware of it and more likely to be on the lookout for suspicious emails sent to you. It should also be less of a surprise if your details get used in one of these fake sender emails.
I know that I say this often but please do NOT use any password for more than one service as that is just asking for trouble. If your details are stolen then criminals will try to use them to access many online services and if you have used the same password then they will be able to access those services.