Blackmail With a Twist
Last Saturday a customer called to say she was concerned about an email she had received. I asked her to forward the email to me as I was certain it would be a type of blackmail email scam. Sure enough when I looked at the body of the email I recognised it as a common type of scam.
Here is the body of the email:
Here is the body of the email:
𝙸 𝚛𝚎𝚚𝚞𝚒𝚛𝚎 𝚢𝚘𝚞𝚛 𝟷𝟶𝟶% 𝚊𝚝𝚝𝚎𝚗𝚝𝚒𝚘𝚗 𝚏𝚘𝚛 𝚝𝚑𝚎 𝚞𝚙 𝚌𝚘𝚖𝚒𝚗𝚐 𝟸𝟺 𝚑𝚘𝚞𝚛𝚜, 𝚘𝚛 𝙸 𝚖𝚊𝚢 𝚖𝚊𝚔𝚎 𝚜𝚞𝚛𝚎 𝚢𝚘𝚞 𝚝𝚑𝚊𝚝 𝚢𝚘𝚞 𝚕𝚒𝚟𝚎 𝚘𝚞𝚝 𝚘𝚏 𝚎𝚖𝚋𝚊𝚛𝚛𝚊𝚜𝚜𝚖𝚎𝚗𝚝 𝚏𝚘𝚛 𝚝𝚑𝚎 𝚛𝚎𝚜𝚝 𝚘𝚏 𝚢𝚘𝚞𝚛 𝚎𝚡𝚒𝚜𝚝𝚎𝚗𝚌𝚎.
𝙷𝚎𝚢, 𝚢𝚘𝚞 𝚍𝚘 𝚗𝚘𝚝 𝚔𝚗𝚘𝚠 𝚖𝚎 𝚙𝚎𝚛𝚜𝚘𝚗𝚊𝚕𝚕𝚢. 𝚈𝚎𝚝 𝙸 𝚔𝚗𝚘𝚠 𝚓𝚞𝚜𝚝 𝚊𝚋𝚘𝚞𝚝 𝚎𝚟𝚎𝚛𝚢𝚝𝚑𝚒𝚗𝚐 𝚊𝚋𝚘𝚞𝚝 𝚢𝚘𝚞. 𝙰𝚕𝚕 𝚘𝚏 𝚢𝚘𝚞𝚛 𝚏𝚊𝚌𝚎𝚋𝚘𝚘𝚔 𝚌𝚘𝚗𝚝𝚊𝚌𝚝 𝚕𝚒𝚜𝚝, 𝚖𝚘𝚋𝚒𝚕𝚎 𝚙𝚑𝚘𝚗𝚎 𝚌𝚘𝚗𝚝𝚊𝚌𝚝𝚜 𝚊𝚜 𝚠𝚎𝚕𝚕 𝚊𝚜 𝚊𝚕𝚕 𝚝𝚑𝚎 𝚍𝚒𝚐𝚒𝚝𝚊𝚕 𝚊𝚌𝚝𝚒𝚟𝚒𝚝𝚢 𝚘𝚗 𝚢𝚘𝚞𝚛 𝚌𝚘𝚖𝚙𝚞𝚝𝚎𝚛 𝚏𝚛𝚘𝚖 𝚙𝚊𝚜𝚝 𝟷𝟻𝟻 𝚍𝚊𝚢𝚜.
𝚆𝚑𝚒𝚌𝚑 𝚒𝚗𝚌𝚕𝚞𝚍𝚎𝚜, 𝚢𝚘𝚞𝚛 𝚖𝚊𝚜𝚝𝚞𝚛𝚋𝚊𝚝𝚒𝚘𝚗 𝚟𝚒𝚍𝚎𝚘, 𝚠𝚑𝚒𝚌𝚑 𝚋𝚛𝚒𝚗𝚐𝚜 𝚖𝚎 𝚝𝚘 𝚝𝚑𝚎 𝚖𝚊𝚒𝚗 𝚛𝚎𝚊𝚜𝚘𝚗 𝚠𝚑𝚢 𝙸 𝚊𝚖 𝚌𝚘𝚖𝚙𝚘𝚜𝚒𝚗𝚐 𝚝𝚑𝚒𝚜 𝚎 𝚖𝚊𝚒𝚕 𝚝𝚘 𝚢𝚘𝚞.
𝚆𝚎𝚕𝚕 𝚝𝚑𝚎 𝚕𝚊𝚜𝚝 𝚝𝚒𝚖𝚎 𝚢𝚘𝚞 𝚠𝚎𝚗𝚝 𝚝𝚘 𝚝𝚑𝚎 𝚙𝚘𝚛𝚗 𝚠𝚎𝚋 𝚜𝚒𝚝𝚎𝚜, 𝚖𝚢 𝚖𝚊𝚕𝚠𝚊𝚛𝚎 𝚎𝚗𝚍𝚎𝚍 𝚞𝚙 𝚋𝚎𝚒𝚗𝚐 𝚊𝚌𝚝𝚒𝚟𝚊𝚝𝚎𝚍 𝚒𝚗𝚜𝚒𝚍𝚎 𝚢𝚘𝚞𝚛 𝚙𝚎𝚛𝚜𝚘𝚗𝚊𝚕 𝚌𝚘𝚖𝚙𝚞𝚝𝚎𝚛 𝚠𝚑𝚒𝚌𝚑 𝚎𝚗𝚍𝚎𝚍 𝚞𝚙 𝚜𝚊𝚟𝚒𝚗𝚐 𝚊 𝚋𝚎𝚊𝚞𝚝𝚒𝚏𝚞𝚕 𝚟𝚒𝚍𝚎𝚘 𝚌𝚕𝚒𝚙 𝚘𝚏 𝚢𝚘𝚞𝚛 𝚖𝚊𝚜𝚝𝚞𝚛𝚋𝚊𝚝𝚒𝚘𝚗 𝚙𝚕𝚊𝚢 𝚋𝚢 𝚊𝚌𝚝𝚒𝚟𝚊𝚝𝚒𝚗𝚐 𝚢𝚘𝚞𝚛 𝚠𝚎𝚋𝚌𝚊𝚖.
(𝚢𝚘𝚞 𝚐𝚘𝚝 𝚊 𝚒𝚗𝚌𝚛𝚎𝚍𝚒𝚋𝚕𝚢 𝚞𝚗𝚞𝚜𝚞𝚊𝚕 𝚙𝚛𝚎𝚏𝚎𝚛𝚎𝚗𝚌𝚎 𝚋𝚝𝚠 𝚕𝚖𝚊𝚘)
𝙸 𝚑𝚊𝚟𝚎 𝚝𝚑𝚎 𝚌𝚘𝚖𝚙𝚕𝚎𝚝𝚎 𝚛𝚎𝚌𝚘𝚛𝚍𝚒𝚗𝚐. 𝙸𝚏 𝚢𝚘𝚞 𝚏𝚎𝚎𝚕 𝙸 𝚊𝚖 𝚏𝚘𝚘𝚕𝚒𝚗𝚐 𝚊𝚛𝚘𝚞𝚗𝚍, 𝚓𝚞𝚜𝚝 𝚛𝚎𝚙𝚕𝚢 𝚙𝚛𝚘𝚘𝚏 𝚊𝚗𝚍 𝙸 𝚠𝚒𝚕𝚕 𝚋𝚎 𝚏𝚘𝚛𝚠𝚊𝚛𝚍𝚒𝚗𝚐 𝚝𝚑𝚎 𝚙𝚊𝚛𝚝𝚒𝚌𝚞𝚕𝚊𝚛 𝚛𝚎𝚌𝚘𝚛𝚍𝚒𝚗𝚐 𝚛𝚊𝚗𝚍𝚘𝚖𝚕𝚢 𝚝𝚘 𝟽 𝚙𝚎𝚘𝚙𝚕𝚎 𝚢𝚘𝚞 𝚔𝚗𝚘𝚠.
𝙸𝚝 𝚖𝚒𝚐𝚑𝚝 𝚋𝚎 𝚢𝚘𝚞𝚛 𝚏𝚛𝚒𝚎𝚗𝚍𝚜, 𝚌𝚘 𝚠𝚘𝚛𝚔𝚎𝚛𝚜, 𝚋𝚘𝚜𝚜, 𝚙𝚊𝚛𝚎𝚗𝚝𝚜 (𝙸 𝚍𝚘𝚗'𝚝 𝚔𝚗𝚘𝚠! 𝙼𝚢 𝚜𝚢𝚜𝚝𝚎𝚖 𝚠𝚒𝚕𝚕 𝚛𝚊𝚗𝚍𝚘𝚖𝚕𝚢 𝚌𝚑𝚘𝚘𝚜𝚎 𝚝𝚑𝚎 𝚌𝚘𝚗𝚝𝚊𝚌𝚝 𝚍𝚎𝚝𝚊𝚒𝚕𝚜).
𝚆𝚘𝚞𝚕𝚍 𝚢𝚘𝚞 𝚋𝚎 𝚌𝚊𝚙𝚊𝚋𝚕𝚎 𝚝𝚘 𝚐𝚊𝚣𝚎 𝚒𝚗𝚝𝚘 𝚊𝚗𝚢𝚘𝚗𝚎'𝚜 𝚎𝚢𝚎𝚜 𝚊𝚐𝚊𝚒𝚗 𝚊𝚏𝚝𝚎𝚛 𝚒𝚝? 𝙸 𝚍𝚘𝚞𝚋𝚝 𝚝𝚑𝚊𝚝...
𝙱𝚞𝚝, 𝚒𝚝 𝚍𝚘𝚎𝚜𝚗'𝚝 𝚑𝚊𝚟𝚎 𝚝𝚘 𝚋𝚎 𝚝𝚑𝚊𝚝 𝚙𝚊𝚝𝚑.
𝙸 𝚠𝚘𝚞𝚕𝚍 𝚕𝚒𝚔𝚎 𝚝𝚘 𝚖𝚊𝚔𝚎 𝚢𝚘𝚞 𝚊 𝚘𝚗𝚎 𝚝𝚒𝚖𝚎, 𝚗𝚘𝚗 𝚗𝚎𝚐𝚘𝚝𝚒𝚊𝚋𝚕𝚎 𝚘𝚏𝚏𝚎𝚛.
𝙿𝚞𝚛𝚌𝚑𝚊𝚜𝚎 $ 𝟸𝟶𝟶𝟶 𝚒𝚗 𝚋𝚒𝚝𝚌𝚘𝚒𝚗 𝚊𝚗𝚍 𝚜𝚎𝚗𝚍 𝚝𝚑𝚎𝚖 𝚘𝚗 𝚝𝚑𝚎 𝚕𝚒𝚜𝚝𝚎𝚍 𝚋𝚎𝚕𝚘𝚠 𝚊𝚍𝚍𝚛𝚎𝚜𝚜:
16aAB4tBJug6NC*7Li9gMNPASx5hz9hwD4B
[𝙲𝙰𝚂𝙴 𝚜𝚎𝚗𝚜𝚒𝚝𝚒𝚟𝚎, 𝚌𝚘𝚙𝚢 𝚊𝚗𝚍 𝚙𝚊𝚜𝚝𝚎 𝚒𝚝, 𝚊𝚗𝚍 𝚛𝚎𝚖𝚘𝚟𝚎 * 𝚏𝚛𝚘𝚖 𝚒𝚝]
(𝙸𝚏 𝚢𝚘𝚞 𝚍𝚘 𝚗𝚘𝚝 𝚞𝚗𝚍𝚎𝚛𝚜𝚝𝚊𝚗𝚍 𝚑𝚘𝚠, 𝚐𝚘𝚘𝚐𝚕𝚎 𝚑𝚘𝚠 𝚝𝚘 𝚊𝚌𝚚𝚞𝚒𝚛𝚎 𝚋𝚒𝚝𝚌𝚘𝚒𝚗. 𝙳𝚘 𝚗𝚘𝚝 𝚠𝚊𝚜𝚝𝚎 𝚖𝚢 𝚒𝚖𝚙𝚘𝚛𝚝𝚊𝚗𝚝 𝚝𝚒𝚖𝚎)
𝙸𝚏 𝚢𝚘𝚞 𝚜𝚎𝚗𝚍 𝚝𝚑𝚒𝚜 𝚙𝚊𝚛𝚝𝚒𝚌𝚞𝚕𝚊𝚛 '𝚍𝚘𝚗𝚊𝚝𝚒𝚘𝚗' (𝚠𝚑𝚢 𝚍𝚘𝚗'𝚝 𝚠𝚎 𝚌𝚊𝚕𝚕 𝚝𝚑𝚒𝚜 𝚝𝚑𝚊𝚝?). 𝙰𝚏𝚝𝚎𝚛 𝚝𝚑𝚊𝚝, 𝙸 𝚠𝚒𝚕𝚕 𝚍𝚒𝚜𝚊𝚙𝚙𝚎𝚊𝚛 𝚏𝚘𝚛 𝚐𝚘𝚘𝚍 . 𝚊𝚗𝚍 𝚗𝚎𝚟𝚎𝚛 𝚌𝚘𝚗𝚝𝚊𝚌𝚝 𝚢𝚘𝚞 𝚊𝚐𝚊𝚒𝚗. 𝙸 𝚠𝚒𝚕𝚕 𝚛𝚎𝚖𝚘𝚟𝚎 𝚎𝚟𝚎𝚛𝚢𝚝𝚑𝚒𝚗𝚐 𝙸 𝚑𝚊𝚟𝚎 𝚐𝚘𝚝 𝚌𝚘𝚗𝚌𝚎𝚛𝚗𝚒𝚗𝚐 𝚢𝚘𝚞. 𝚈𝚘𝚞 𝚖𝚊𝚢 𝚔𝚎𝚎𝚙 𝚘𝚗 𝚕𝚒𝚟𝚒𝚗𝚐 𝚢𝚘𝚞𝚛 𝚌𝚞𝚛𝚛𝚎𝚗𝚝 𝚘𝚛𝚍𝚒𝚗𝚊𝚛𝚢 𝚍𝚊𝚢 𝚝𝚘 𝚍𝚊𝚢 𝚕𝚒𝚏𝚎𝚜𝚝𝚢𝚕𝚎 𝚠𝚒𝚝𝚑 𝚊𝚋𝚜𝚘𝚕𝚞𝚝𝚎𝚕𝚢 𝚗𝚘 𝚌𝚘𝚗𝚌𝚎𝚛𝚗𝚜.
𝚈𝚘𝚞'𝚟𝚎 𝚐𝚘𝚝 𝟸𝟺 𝚑𝚘𝚞𝚛𝚜 𝚒𝚗 𝚘𝚛𝚍𝚎𝚛 𝚝𝚘 𝚍𝚘 𝚜𝚘. 𝚈𝚘𝚞𝚛 𝚝𝚒𝚖𝚎 𝚜𝚝𝚊𝚛𝚝𝚜 𝚘𝚏𝚏 𝚊𝚜 𝚜𝚘𝚘𝚗 𝚢𝚘𝚞 𝚐𝚘 𝚝𝚑𝚛𝚘𝚞𝚐𝚑 𝚝𝚑𝚒𝚜 𝚎𝚖𝚊𝚒𝚕. 𝙸 𝚑𝚊𝚟𝚎 𝚊𝚗 𝚜𝚙𝚎𝚌𝚒𝚊𝚕 𝚌𝚘𝚍𝚎 𝚝𝚑𝚊𝚝 𝚠𝚒𝚕𝚕 𝚊𝚕𝚎𝚛𝚝 𝚖𝚎 𝚊𝚜 𝚜𝚘𝚘𝚗 𝚊𝚜 𝚢𝚘𝚞 𝚐𝚘 𝚝𝚑𝚛𝚘𝚞𝚐𝚑 𝚝𝚑𝚒𝚜 𝚎𝚖𝚊𝚒𝚕 𝚝𝚑𝚎𝚛𝚎𝚏𝚘𝚛𝚎 𝚍𝚘𝚗'𝚝 𝚊𝚝𝚝𝚎𝚖𝚙𝚝 𝚝𝚘 𝚊𝚌𝚝 𝚜𝚖𝚊𝚛𝚝.
I have seen a lot of emails similar to this one, even received a few myself, and they are sent out by scumbags that hope a few of the recipients will believe that the claims are genuine and pay up. Unless you are extremely gullible or you have been visiting pornographic websites it should be very obvious that the claims in the email are false.
However, one thing about this email is different to all of the examples I have seen or received. This email has a password in the Subject field and in the first line of the body of the email:
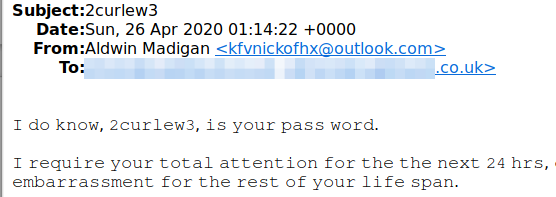
The recipient recognised the password as belonging to a LinkedIn account. Not knowing how the scammer had obtained her email address and LinkedIn password prompted her to call me for advice.
The scammer has included this password to try and convince the recipient that all of it must be genuine because the password is the correct one for her LinkedIn account. Notice though that no part of the email specifically mentions LinkedIn and no other passwords are included.
So how has the scammer obtained this password?
The scammer has simply used a list of stolen email addresses that also include their corresponding passwords. LinkedIn had about 164 million account details stolen on the 21st May 2016 and it appears that this is the data the scammer is using to target people with this email. My customer has not used her LinkedIn account for a long time so she had not changed the password after the 2016 data breach occurred.
With so much stolen data available to scammers it is very easy to do something like this. One database of stolen data contains more than 770 million email addresses and passwords. This is valuable for hackers because some recipients will see a genuine password and assume that other claims in an email must be true. They won’t realise that the password is from a stolen list and that other claims are all bogus.
Keeping tabs on your on-line accounts.
Every single day data will be stolen from one or more on-line services. Far more email addresses and passwords are obtained in this way than from hacking into peoples computers and other devices. So it is really important that you are aware of any data loss that involves your own details. Don’t assume that the organisations that lose the data will inform you about any breach as often they don’t know for weeks or months after it has happened.
Some will also keep quiet for a period after any breach whilst they try to work out what has been stolen and how they are going to mitigate the impact on their organisation. Quite often the stolen data is found on hacking website long before the hacked organisations tell users about the problem.
One excellent service that I use and recommend is called Firefox Monitor. It is free to use and is very simple to setup. If you don’t already have a Firefox account you can sign up and then you are able to add all your email addresses to their Monitor service. If your email address is found in any stolen data located by their service you will be notified so that you can resolve the issue.
I have four email addresses being monitored by their service as you can see below:
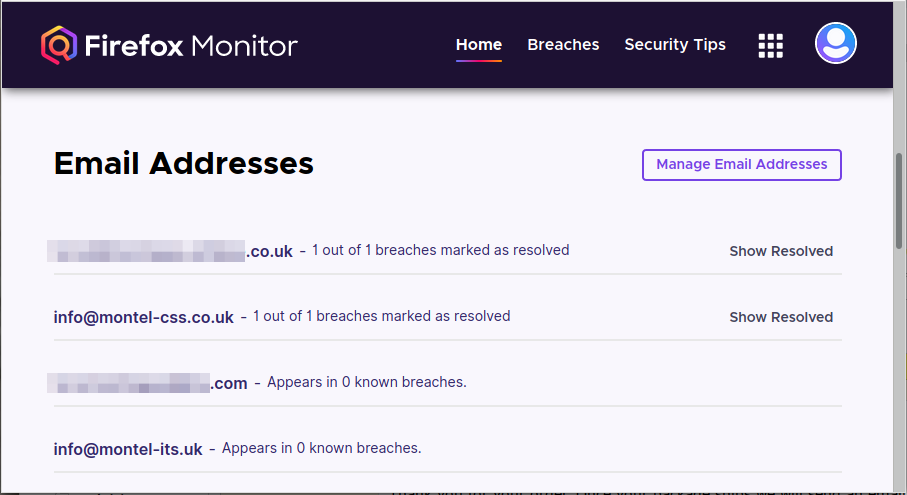
When I signed up for the service I discovered that two of my email addresses had been found in data breaches of two services. The Firefox Monitor service made it very easy for me to resolve these two problems. It even allows me to mark them as resolved so I have a history of what services have been breached and an indication that I have dealt with it.
To join the Firefox Monitor service and add your own email addresses just go to:
https://monitor.firefox.com/
If you already have a Firefox account just sign in and then add your email addresses. If you don’t have a Firefox account its free to sign up and your details will be kept private and secure. Put your email address into this service right now so you know if it has already been found in any of the published lists of stolen data.
The folly of using one password.
Some people are foolish enough to use a single password for more than one service. Hopefully, you are not one of them. If you only use one password as soon as it is stolen the criminals will be able to access all the services that use the same password. You probably won’t find out about it being stolen until it is too late. If or when you do find out that your password has been stolen you will have to change it on every service you have used it on.
As I use unique passwords for all of my on-line services, and I have hundreds of them, when I found out about the two data breaches I only needed to change those two passwords. If you want to get an idea of how many breached services are already covered by the Firefox Monitor service go to:
https://monitor.firefox.com/breaches
Scroll down to the bottom of the page and then click the Show all button. One look at that long list of breached sites should tell you that sooner or later an on-line service you use will be hacked. Be sensible and use unique passwords for each service you sign up to and when the inevitable happens you won’t have to spend hours changing passwords.
Don’t use patterns in your passwords.
If you look at the password used in this scam email, the one used for a LinkedIn account, you should be able to see how it has been created. There is a pretty obvious pattern that any good hacker will spot and will then try to exploit. Passwords built with patterns are not as strong as they may seem as it is quite easy to configure a password cracking tool to attack a service or protected data file using guesses based on the likely pattern discerned from a stolen password. This is far easier to do than you may think.
Take a look at this short and easy to follow video on YouTube to see just how easy it is to configure password attack tools:
https://www.youtube.com/watch?v=fPHkO6T_g8A
The very first tool he describes, called Cewl, should stop you from ever using passwords with an obvious pattern in them. If it doesn’t then the second tool he describes, called Crunch, should do the trick. If you watch the video you will definitely think about how good your own passwords really are. The person who made this video is an ethical hacker and is not trying to teach people how to hack systems. You can use these tools for good or evil and in this case he is showing how they can be put to good use.
If you want advice or help to improve your own password security then get in touch.