Genuine or Fake?
Take a look at this email.
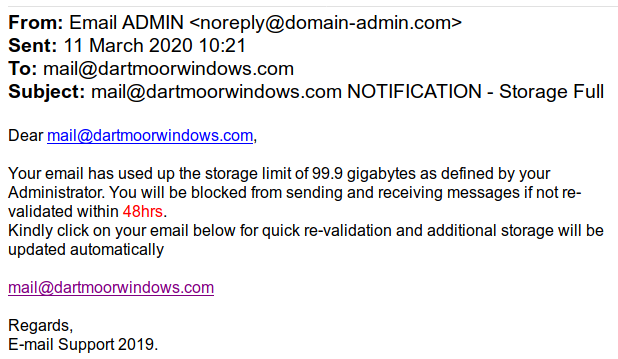
Is it genuine or a fake?

Is it genuine or a fake?
Let’s see how well you have done.
If you decided that it is a fake within a few seconds then you are not likely to be taken in by fake emails like this one. Just remember that many scam emails will look far more convincing than this one so don’t get complacent.
If you weren’t sure if it is genuine or not then you are much more at risk of being caught out by scam emails like this one. You are also more likely to be caught by a scam email that looks a lot more genuine than this one so you need to learn how to spot them if you want to avoid becoming a victim of cyber crime.
If you thought this email is genuine then you have either already been scammed or you will be in the near future. This email is shouting FAKE so if you don’t want to be a victim you really do need to find what to look for in any email to be able to spot the fakes.
What is it that says it is a fake?
The first thing I always look for is some information about the sender. Does the email have an organisations name, logo, address, contact details and anything else to say who might have sent it. This email is devoid of all such identifying information and is striking simply because it has nothing at all to show who has sent it. Any email that is as anonymous as this one should always be treated with a high degree of suspicion. In this example the lack of information is the first red flag.
Just remember that scammers will often go to great lengths to make their emails appear genuine and will incorporate all of these things to fool you into thinking that an email is genuine. Having all these things does NOT mean that any email is genuine but the complete lack of them is a very good indicator that it may not be.
Who is it from?
The next thing I look at is the From: details as these often give away the real identity of the sender. When you receive an email your email software or system can show you one or two different bits of information. Here is the technical explanation of what is displayed and why:
In RFC 5322, section 3.4. Address Specification, it states that email addresses must be enclosed between angle-brackets < > if display names are also used.
A display name is the human friendly name that any sender can have so my email display name can be Terry Montague. I can use anything as my display name so it would be very easy for a scammer to use any name as this cannot and is not checked by any email system.
However, the senders email address, the parts between the < > brackets, is not easy to fake and this will often give away the identity of the email account used to send the email. Make sure that your email system ALWAYS displays the full email address and not just the display name as a failure to do so makes it far more likely that you will be taken in by a scam email.
Always look at the address between the brackets and make sure it matches the usual email address for the sender. Often you will see a display name like Fred Smith but something completely different in the full sending address. That is an easy way to spot a scam email.
In our email the display name is Email ADMIN and the full sending address is noreply@domain-admin.com
We can discount the display name as it is trivial to fake so we need to look at the sending address. In our email it appears to be a domain name that tells us nothing about the senders identity. I’m pretty sure this is a fake name as GoDaddy will sell me this domain name for £624 so I’m assuming that it is currently available to buy.
Given that what appears to be the senders address tells us nothing about the senders identity this is another big red flag when deciding if the email is genuine or not.
The next step is to look at the body of the email.
Does the email require the recipient to take some action in a limited time?
This is a tactic frequently used by scammers as they want you to do something quickly so you don’t have time to think about it. In our email the scammers are saying that the recipient only has 48 hours and they have emphasised this by putting the 48hrs in red. Yet another red flag for this email.
Does the email contain any links to click on?
Yes it does. In this email we are told that clicking on the link will quickly revalidate the account and additional storage will be updated automatically. The very existence of a link in any email should always be a red flag no matter who you think has sent it. You could have an email from the Pope but if it has a link in it then ALWAYS treat it as suspicious.
The next test is very easy to do. Just hover the mouse over any link without clicking on it. Now you should be able to see the exact location the link is pointing to. In our email it looks like the link will point to an email account but a link can be made to say anything at all. It is only when you hover over a link that you will see where it is going to go if you click on it.
When I hovered over this link it showed the true location as:
https://manupol.com.co/imagenes/galeria/55000fr/ypoo/dcdd/?email=mail@dartmoorwindows.com
Does that look like the email address in the email?
I don’t think so. That is a huge red flag and proves beyond doubt that this is a scam email. In this case it is a phishing email intended to steal the password for the mail@ email account.
If you look at the domain name in the real location it ends with .co and that is the Internet country code for Colombia. In this case the criminals have hidden their fake logon page inside the website of a genuine business in Colombia. This is something criminals frequently do to try and avoid detection for as long as possible.
In most circumstances I would describe this email as a rather crude and lazy attempt by the criminals. They don’t appear to have made any effort to make this email appear genuine so spotting it as a fake has been very easy. You would have to be very gullible to fall for this one.
Yet this email is actually more sophisticated than it seems as is the scam behind it.
I think this particular email has been designed to look like it does because the scammers think they know what sort of email system and client the recipient is using.
Why do I think this?
I used one of my safe machines, running a version of Linux, to open the email and click on the link it contains. This took me to a web page showing the Roundcube logon screen as shown below:
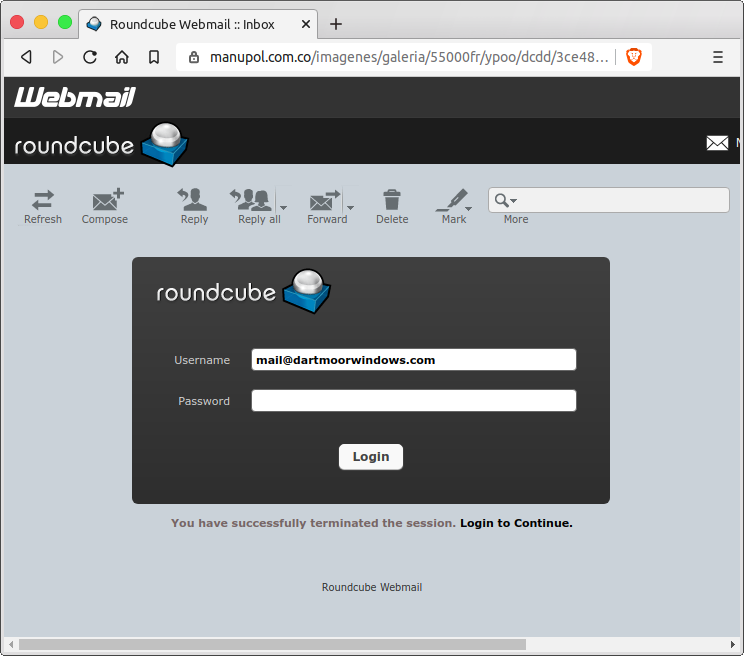
Now that came as something of a surprise to me because if the user was not using Roundcube as their email client software surely they would be suspicious of an unusual screen and be far less likely to put their password in. Only the most gullible user would be daft enough to enter a password on a screen they had never seen before and the criminals would be greatly reducing the chance of their scam working.
The thing is that I know that this user did use Roundcube for a short while before we migrated their email system to another service. So far from being crude and lazy I think this scam is actually rather sophisticated as the scammers have clearly looked at peoples email clients and then designed a system that will show a potential victim a logon screen they will probably be familiar with. That makes the chances of someone thinking it is genuine far higher.
Here is the other reason I think this is actually a sophisticated and well planned attack. Take a look at the full URL for the web page shown above:
https://manupol.com.co/imagenes/galeria/55000fr/ypoo/dcdd/3ce48d25715c2ba31a7dd180cec1917e/road.php?https://cpsess1530024440/webmail/paper_lantern/index.html?mailclient=roundcube%2Fmail&service=mail&flowName=GlifWebSignIn&flowEntry=AddSession
Notice anything?
Look again at this one:
https://manupol.com.co/imagenes/galeria/55000fr/ypoo/dcdd/3ce48d25715c2ba31a7dd180cec1917e/road.php?https://cpsess1530024440/webmail/paper_lantern/index.html?mailclient=roundcube%2Fmail&service=mail&flowName=GlifWebSignIn&flowEntry=AddSession
It looks like each link is being directed to a logon page based on the recipients usual email system. I bet if the email recipient is using Microsoft Outlook on Office 365 then the logon page displayed will be a copy of the normal Office 365 page.
This is clever and not something I have seen before.
Of course the email itself is full of red flags so spotting it as a scam is easy. If you remember these checks and apply them to all the emails you receive then it will be much more difficult for the scammers to trick you into becoming a victim of phishing. It’s a lot easier to spot them when you know how to.